I have been really busy and have therefore not posted in a while. Work has really consumed me and I was studying to take the CEH (Certified Ethical Hacker) on Dec. 1st. Which a am very proud to say that I am now a Certified Ethical Hacker! Well, I have spent a lot of time working on fuzzers and ways to make my penetration testing more efficient. I have recently discovered the scripting options in webscarab (written by Rogan Dawes) and been trying to make some use of this feature. What I wrote was simple script that once an XSS exploit has been found it will write a screen scrape of that page to the file system. This way you can quickly identify which attacks worked and which ones did not using the Fuzzer plugin within WebScarab. Here is the script:
import org.owasp.webscarab.model.ConversationID;
import org.owasp.webscarab.model.HttpUrl;
import org.owasp.webscarab.model.Request;
import org.owasp.webscarab.model.Response;
import java.text.DateFormat;
import java.text.SimpleDateFormat;
import java.io.BufferedReader;
import java.io.BufferedWriter;
import java.io.FileReader;
import java.io.FileWriter;
import javax.swing.JOptionPane;
String xssFile = "/home/ascetik/xss.txt";
// Load xss strings
DateFormat df = new SimpleDateFormat( "yyyyMMdd-hhmmss" );
String date = df.format(new java.util.Date());
String outFile = "/home/ascetik/screenScrapes/ss-" + date + ".html";
// save file based on date
BufferedReader xssStrings = new BufferedReader(new FileReader(xssFile));
BufferedWriter bfOut = new BufferedWriter(new FileWriter(outFile));
Response response = conversation.getResponse();
// conversation Response
Request request = conversation.getRequest();
// conversation Request
byte[] hexResp = response.getContent();
// get the screen scrape
String raw = new String(hexResp);
// convert it to string
// Test the Response to see if our string is echoed back
String xss;
while ((xss = xssStrings.readLine()) != null) {
if ( raw.indexOf(xss) != -1 && xss != "") {
bfOut.write(raw);
bfOut.close();
//JOptionPane.showMessageDialog(null, "Possible XSS Found");
}
}
Now let me explain. This script is run after the response is received from the server. I have a file called xss.txt that contains xss exploits that I also use as the input source for the Fuzzer plugin (i'll explain more later) but I also use it in this script to search for the strings in the server response. If the string is found in the response there is a fairly good chance the exploit was successful.
When one of the xss string is found I write an html file that is a screen scape of the response and the file name looks like “ss-20071201-041504.html”. Which is ss + the date and time down to the second.
To use this script you need to load it to the webscarab framework via Tools->Script Manager at the top of the WebScarab application.
Then there is a tree view that displays Framework->AddConversation.
Click Add at the top.
Now every time a conversation is added to the Summary of WebScarab this script will run as long as the checkbox is selected next to the script in the Script Manager.
 Using the Fuzzer
Using the FuzzerOnce you have the above script loaded in the Script Manager go to the Summary tab and find a conversation that you want to fuzz. You can look at the parameters column to find a fuzzable request. Now right click and select Use as fuzz template. Select the Fuzzer tab now and you will see your request added here with all the parameters broken out.
Click Source in the middle of the Fuzzer plugin and add the same xss.txt file that you have listed in the above script. Once this is done you can use this file to fuzz the parameters in the fuzz template.
Select the fuxx source for each parameter from a drop down box.
Now click start. If any of your fuzzing executed an XSS you will see files appearing in your folder you assigned in the Script Manager.
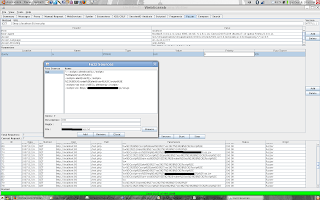
As you can see this can be used for several different things. You could have sql injection strings listed in the fuzzer sources and then have partial sql error messages be in the file you use as input to the script you added to the Script Manager. Once you know your way around WebScarab and which hooks are available you are only limited by your imagination.
More on Webscarab and Scripting.In the script manager you will see descriptions of the hooks available to you. I just explained the conversation options but there are Proxy options as well. You can have special scripts run on both the request and response for the proxy. I used the conversation because I could not query the responses from the fuzzer plugin via the proxy scripts. Some ideas I have thought about implementing are alerts that pop up when patterns in the responses like hidden error messages, ip address strings, etc. are found.





