FuseSoft develops Assessment Collaboration, Vulnerability Management, and Assessment Automation software. The idea is to automate much of the overhead from penetration testing teams so they can get back to finding more bugs instead of writing reports, managing assessment scheduling, or keeping up with retesting, etc. They include collaboration and workflow enhancements into burp suite and in many cases you can enter all your findings right from burp and never have to log into the actual site. Default vulnerability information is repopulated for you by the tools so you don't have to rewrite or copy/paste descriptions and remediation recommendations for issues like XSS or SQLi or many others that you find assessment after assessment.
Below is the main Dashboard. Assessors have access to all of their current assessment and retest queues. There is even a "Your Week" box a the bottom that holds your current assessment scope and information. The idea is that all the information is pre-populated and ready for you to start hacking as soon as you log in on Monday morning. It even displays the other assessors who are working with you that week.
You can open an assessment to view the details and add vulnerabilities. There is a running total of all issues discovered at the top of the screen. Entering vulnerabilities common vulnerabilities will pre-populate the boiler plate text.
But your not restricted to just using the website to enter vulnerabilities. There is some pretty robust burp suite integration. You can add vulnerabilities and extracts of the vulnerable payloads just by selecting response text and right clicking. It has the option to upload the request and/or response as well as snip out cookie information.
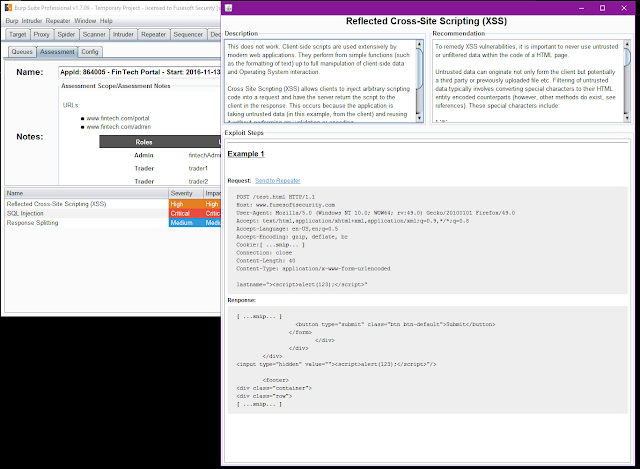
For example say we found XSS on a site. We have fully exploited it in burp repeater. Just right click, search for the XSS default vulnerability, and even add exploit steps all from inside Burp.
The message box supports the Markdown Syntax so you can do some light report editing right from inside burp. The result will look like the following screenshot on the web version.
Notice our exploit Steps have been converted to Rich Text, We have an example payload. We also have the full Request and only the selected response extracted. You can then perform further edits like highlight the specific exploit RED so that its easier to identify.
All of this goes from the WYSIWYG editor to DOCX reports. Below is an example extract of the MS Word Report.
The enhancements don't stop there either. The burp plugin will update in mealtime to display all new findings being discovered. During collaborative assessments you can see what other issues other users are finding and you can even replay their payloads.
Below is an example of the vulnerability history for this application that is being tested. You see all issues from previous assessments and the new issues that your fellow assessors are finding. If you click any vulnerability in the table you will be presented with the full description and exploit steps.
The Burp plugin detects if its a valid payload that can be replayed and creates a link above the request. This allows the current assessor to replay with just a click. Notice below the hyper link above the request that displays 'Send to Repeater'.
You get this same functionality with retests as well. If a verification retest is assigned to you then you can pull of the previous assessment's payload and replay it. This saves you the time of trying to find previous Burp states and correct requests that were used to exploit the vulnerability originally taking a lot of the guess work out of retests.
In addition to the ability to just replay existing vulnerabilities via burp, it can also allow you to send repeater items, site maps, proxy history, and scan items directly to another user. You can right click the item or items and then just select other online users and they will show up in their Burp session.
In the below screenshot we can take this exact repeater request and send to another user's repeater.
The Title you add will display as a new Repeater tab title. This is useful for collaborating on finding an valid exploit payload.
Report Generation and Peer Reviews:
I discussed briefly the report generation features above but there is more! You can upload your current reporting templates and Faction will output reports in those styles. There is a huge selection of variables that can be inserted into your original templates that will be replaced with assessment data.
More information on that can be found here.
After reports are generated they can be added to the Peer Review Queue. This allows your peers to make changes to your reports before you finalize and send them out to the application owners. It allows your peers to strike out text or added notes to the side regions to alert you of issues. Its a typical change tracking functionality that you would find in Word but all web based.
Vulnerability Management:
Vulnerability Management teams have a queue that shows all vulnerabilities assigned to them for remediation that are approaching due dates, gone past due, are out to assessors for retest, and retests that have gone past due.
They can also search for vulnerabilities and add notes about them, close them in development and/or close them in production.
Assessment Scheduling:
Faction keeps track of all your assessors schedules and will alert you when an assessor is not available for the next big assessment. The system shows all assessors and annotates the user as [Not Free] to ensure you don't select them when they are off on other projects. You can still add them to an assessment even if they are not free though.
There are forms to update the scope for the assessment and add files that might be required. This ensures that the assessor has all the information they need when they start the assessment.
But wait there is more:
Faction has a full REST API and a event based API that allows it to integrate with other systems. The even based API allows you to write python code to integrate with existing tracking systems or application inventory systems.
The Rest based API will allow you to schedule assessments, query applications and vulnerabilities, and much more. The Faction Burp plugin was developed to use this API.
Conclusion
Check it our while its still free. Its a fully developed assessment workflow and collaboration engine that runs on a Tomcat Server with a Mongo backend. Really easy to install and use.
Find out more at the FuseSoft Security Site.














No comments:
Post a Comment